In the modern digital landscape, the rise of CEO email Impersonation Scams poses a severe risk to businesses and their financial stability. This insidious scam involves perpetrators impersonating a company’s CEO to deceive employees or clients into divulging sensitive information or making unauthorized payments. The repercussions of falling victim to such fraud can be catastrophic, leading to substantial financial losses, tarnished corporate reputations, and a loss of trust among stakeholders.
The Tale of Sarah: A Victim of CEO Email Cloning Fraud
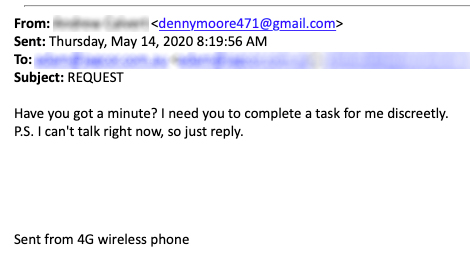
Consider the plight of Sarah, a small business owner operating a thriving e-commerce venture. One fateful day, Sarah received an email seemingly from her CEO, urgently requesting a substantial funds transfer to a purported new supplier. Despite feeling pressured, Sarah complied with the request, only to later discover that the email was a sham. Sarah had become a victim of CEO email cloning fraud, with the scammer leveraging a deceptively similar email address to dupe her into transferring funds.
The Anatomy of CEO Email Cloning Fraud
The process behind CEO email cloning fraud is orchestrated with meticulous planning:
Research Phase
Fraudsters meticulously research their target company and its personnel, gathering intelligence on the CEO and other key figures. This information serves as the foundation for crafting convincing email impersonations.
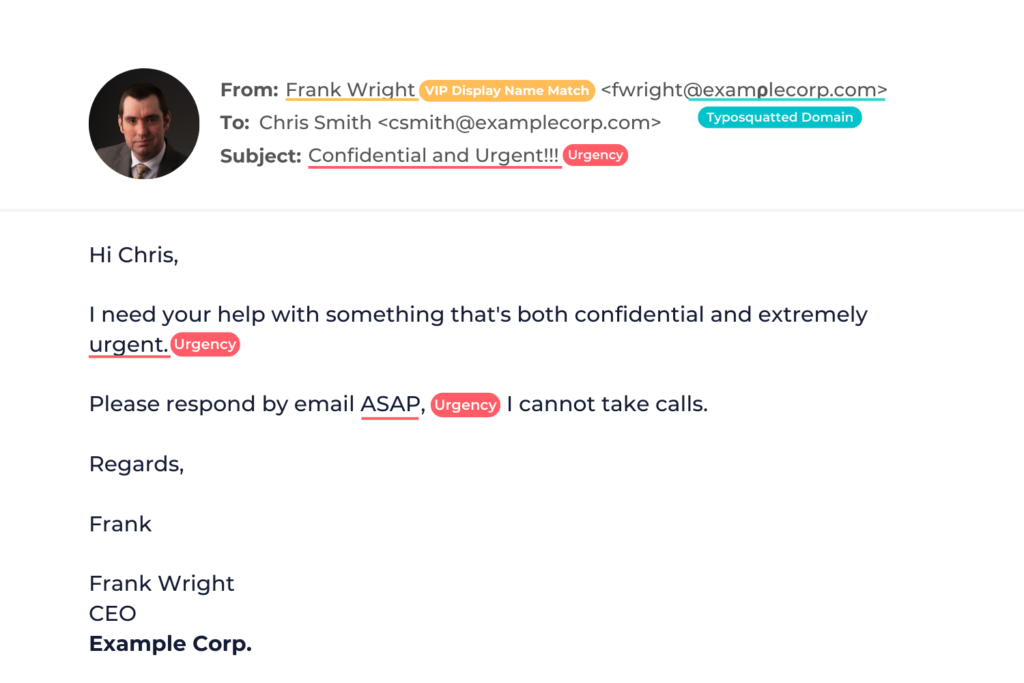
CEO email Impersonation Scams: Email Cloning
Armed with acquired knowledge, the fraudster creates an email address resembling that of the CEO, often employing subtle alterations in spelling or structure. This cloned email address is then utilized to dispatch seemingly authentic emails purportedly from the CEO.
Urgent Solicitation
The fraudulent email typically contains an urgent request for sensitive information or monetary transactions. Leveraging a sense of immediacy, the scammer coerces recipients into complying with the illicit demands.
Financial Exploitation
Should the recipient fall prey to the ruse and furnish the requested information or funds, the fraudster gains access to valuable assets or confidential data, perpetuating the deception.
Mitigating the Risk: Strategies Against CEO Email Cloning Fraud
Sarah’s ordeal resulted in substantial financial setbacks and reputational damage, leaving stakeholders questioning the security of her company’s operations. This unfortunate incident served as a wakeup call for Sarah, prompting her to advocate for greater awareness and prevention of CEO email cloning scams.
Employee Education
To mitigate the risk of falling victim to CEO email cloning fraud, businesses must adopt a proactive, multi-pronged approach to fortifying their email infrastructure. Here are key steps companies can take to bolster their defenses:
Two-Factor Authentication
Implement two-factor authentication protocols to enhance the security of email accounts. This additional layer of verification reduces the likelihood of unauthorized access and diminishes susceptibility to CEO email cloning fraud.
Verification Protocols
Enforce stringent verification procedures for email requests involving sensitive transactions or data disclosures. Encourage employees to authenticate purported CEO directives through direct communication channels before taking action.
Email Monitoring
Employ robust email monitoring systems to scrutinize incoming and outgoing correspondence for irregularities indicative of fraudulent activity. Vigilant oversight enables swift detection and mitigation of CEO email cloning attempts.
Secure Email Providers
Entrust email communications to reputable service providers offering advanced security features such as end-to-end encryption and real-time threat detection. Select providers equipped with robust anti-phishing measures to fortify defenses against email-based attacks.
Regular Software Updates
Maintain the integrity of email systems by routinely updating software and security protocols. This includes implementing patches for vulnerabilities and ensuring the latest antivirus software and firewalls are deployed.
Strengthening Resilience Against CEO Email Cloning Fraud
In conclusion, CEO email cloning fraud represents a grave menace demanding the attention of businesses across all sectors. The ramifications of succumbing to such scams are profound, encompassing financial turmoil, reputational harm, and eroded stakeholder confidence. Through heightened vigilance, robust security measures, and ongoing education, businesses can fortify their resilience against CEO email impersonation scams, preserving their integrity and prosperity in an ever-digital world.